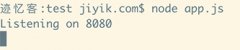
Running a Docker instance from a Dockerfile
Publish Date:2025/03/26 Author:JIYIK Category:Docker
-
Docker containers have undoubtedly become the standard unit for managing software and dependencies in different environments. When using real applications, you must create a docker file before building the container image of the application...
Full